What is a macro virus? + How to remove one

No matter what computer or operating system you have, macro viruses can attack you. This type of computer virus will launch its malicious code as soon as you open an infected file. Keep reading to learn about malware-infected macros and how to remove a macro virus. Then download Norton 360 Deluxe to help protect your device against macro viruses, suspicious links, and other online threats.
What is a macro virus?
A macro virus is a type of computer virus that’s written in the same macro language used to automate tasks in software programs like Word, PowerPoint, and Excel. These types of viruses aren’t specific to one operating system (OS), as malicious macros can be found in documents, spreadsheets, or links.
How macro viruses work and spread
When an infected file is opened or a malicious link is clicked, the macro virus releases a sequence of commands that execute automatically. This can lead to data corruption or data loss and system instability. Macro viruses can self-replicate and spread.
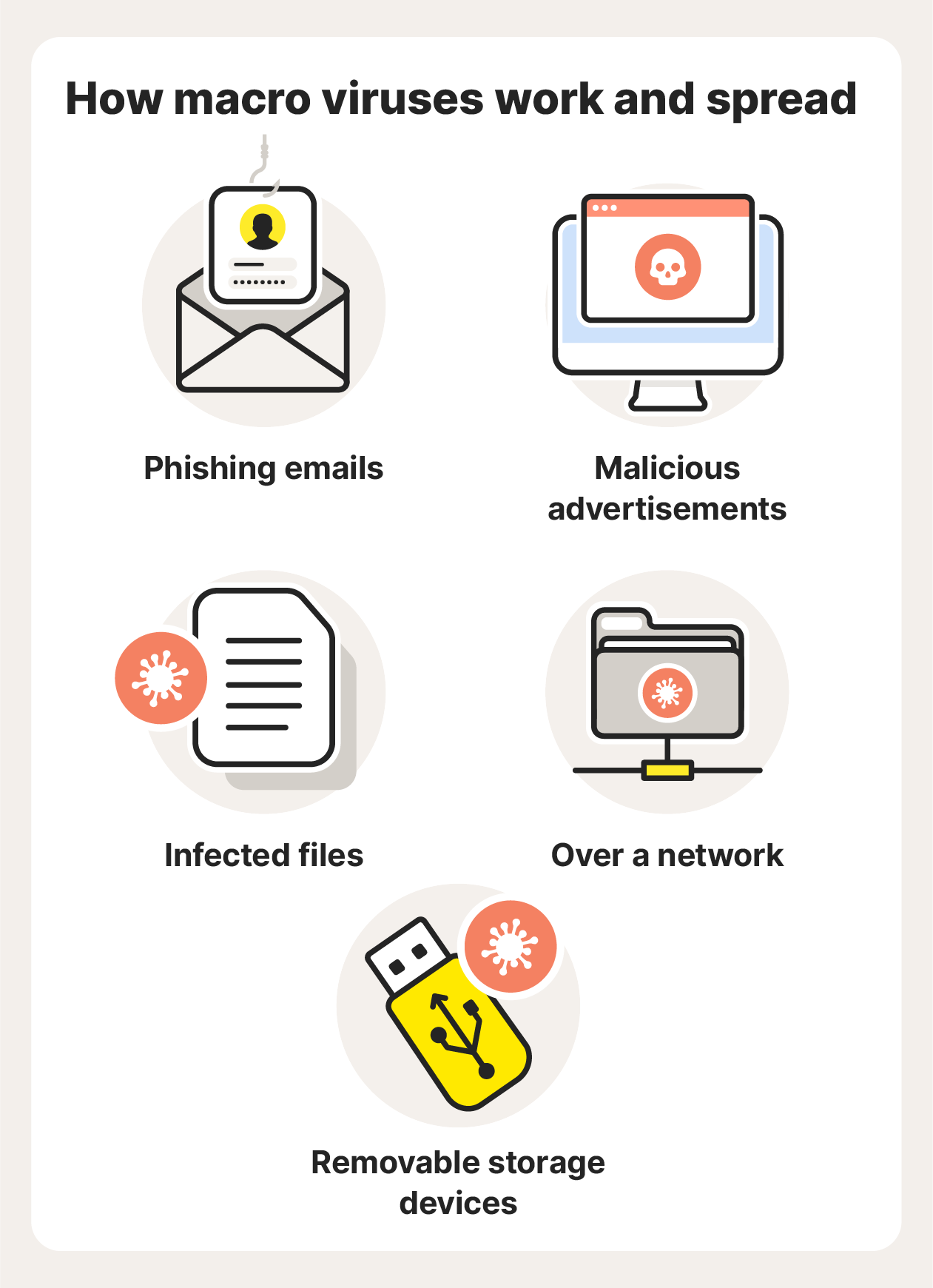
Here are the main ways malicious macros can find their way onto your device:
- Phishing emails: Macro viruses are often spread through phishing emails containing attachments that have been infected with the virus. Some macro viruses can then continue to spread by accessing the data in a victim’s address book and sending further phishing emails to people on their contact list.
- Malicious advertisements: Spoofed ads can include infected links or downloads that spread a macro virus to your device. Always check the URL before you click an online ad and learn how to avoid malvertising and steer clear of malicious websites.
- Infected files: Macro viruses spread when a user with macros enabled opens an infected document. If you open a file that contains a malicious macro, that virus can spread to other files on your device. If you email or share an infected file with someone else, they too will have that macro virus if they open the file.
- Over a network: If an infected file is saved to a shared network drive, then any user who opens that file will also get the virus.
- Removable storage devices: If an infected file is shared on a removable media device like a USB flash drive, the infection will spread to the computer of any user who opens the file.
Dangers of macro viruses
A macro virus can do a lot of damage to the files on your computer. But it can also be more invasive, even nefariously accessing email accounts and sending out infected emails to your contact list, spreading the macro virus to other devices.
Some of the dangers of macro viruses include the ability to:
- Create new files
- Corrupt or delete data
- Move files
- Format hard drives
- Access email accounts
- Send files to others via email
- Deliver destructive viruses and malware
Macro virus examples
Here are some real-life examples of macro viruses, some of which have done considerable damage:
- Concept virus (1995): The Concept virus spread through Microsoft Word documents and was the first widespread macro virus. Because it only displayed a benign message on the screens of infected computers, it didn’t do much damage. But the Concept virus was difficult to get rid of and showed the potential impact such malicious software could have.
- Melissa (1999): The Melissa virus, which emerged in 1999, is a now-classic example of a macro virus. Downloading an infected document triggered Microsoft Outlook to send messages with an infected attachment to the first 50 email addresses in a user’s contact list. The virus replicated at an extraordinarily fast rate and caused around $80 million in damage.
- Hancitor (2014): Also known as Chanitor, the Hancitor virus used a Word document to release its payload, and it delivered other malware like Trojans that were downloaded silently in the background.

Macro viruses usually infect Microsoft Office files.
How to spot a macro virus
It can be difficult to spot macro viruses in advance because they’re only activated once you open an infected file or link. But there are some signs that can indicate that you might have a macro virus, so pay attention to the way your computer behaves and any files you interact with.
Here are a few virus warning signs that could signal your computer is infected with a macro virus:
- Your computer starts running slower than usual.
- Files that don’t usually ask for passwords ask for one.
- Your computer saves documents as “template” files.
- Strange error messages start displaying.
- You get unexpected prompts to enable macros.
How to prevent macro viruses
As with biological viruses, prevention, though not foolproof, is usually the best cure. Use the following tips to help protect your computer and safeguard your files:
- Enable spam filters: Turn on email spam filters to flag suspicious emails and attachments to help you avoid accidentally clicking and downloading a virus.
- Update software: Regularly run or automate software updates, as these can fix glitches and patch security flaws.
- Update your OS: Update your computer’s operating system when new versions are released.
- Avoid suspicious links and attachments: Never click a link or attachment in an email unless you’re expecting it and are sure it’s not a spoofed email. Before you click, verify that the destination URL is safe.
- Disable macros: Protect yourself in case you accidentally open an infected file by disabling macros by default. Do this for any application that uses macros. If you need to enable them later for whatever reason, you can always do so.
- Use antivirus software: Use trusted antivirus software to help protect against suspicious links, hackers, viruses, and other threats.
Let Norton 360 Deluxe be your first line of defense against viruses and malware. With powerful protection against hackers, dangerous links, and viruses, Norton 360 Deluxe provides award-winning security to help you block threats and protect your device.
How to remove a macro virus from your device
You have a couple of different options if you think your device is infected with a macro virus:
- Use antivirus software: Use reliable security software like Norton 360 Deluxe to help remove malware like macro viruses. Norton 360 Deluxe can also help block malware from hitting your device in the first place, so it’s good digital hygiene to have a reliable antivirus running on your devices.
- Manual removal: Start your computer in Safe Mode to protect your device while you look for viruses. Use a virus scanner and removal tool to help find malware on your computer, then delete the infected program or file.
Protect your devices from macro viruses with Norton 360 Deluxe
Understanding how macro viruses work is crucial to avoiding infection. But like all malware, macro virus strains can evolve quickly. And no one is completely immune. Convincing phishing schemes that try to trick you into clicking infected links are seemingly all over. That’s one reason it’s so important to level up your protection with reliable security software.
Norton 360 Deluxe provides powerful online protection to help keep macro viruses and other malware off your device. Plus, it has a suite of built-in features, like a VPN to encrypt your connection and secure the data you send and receive online.
FAQs about macro viruses
Macro attacks can cause a great deal of damage, so it’s important to be aware of what they are and how they work. Here are some FAQs to help you understand macro viruses further.
Can Macs get macro viruses?
Yes, Macs can get malware like macro viruses. Because macro viruses are based on an application rather than an operating system, they can infect devices on any operating system, including non-Windows computers.
What is a Microsoft Word macro virus?
A Microsoft Word macro virus is a computer virus written in the same macro language that Microsoft Word uses. When an infected Word file is opened, the macro virus triggers an automatic sequence of actions. These actions can cause damage to the computer and its applications.
How have macro viruses evolved?
Early macro viruses were fairly simple and benign. Since then, their complexity has increased, and they can now cause serious damage and are used to deliver malware such as trojans or ransomware. While they were originally developed to target Microsoft Office apps, macro viruses can now be hidden in other software and links, too.
What computer programs are most affected by macro viruses?
Macro viruses usually infect Microsoft Office apps like Word, Excel, and PowerPoint. But they can affect any computer program that supports macros.
Are macros a type of malicious code?
Macros themselves are not a type of malicious code; they are sets of instructions written within software to automate certain functions. Malicious code can be embedded within macros and cause damage when the macros are running, which is called a macros virus. But safe and helpful macros are used all the time to automate tasks and add functionality to forms, spreadsheets, and other documents.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips and updates.